 Schilling Show Blog Readers, let me ask you a few questions.
Schilling Show Blog Readers, let me ask you a few questions.
Have you ever watched a video online or downloaded one to one of your devices? Then you likely have used ffmpeg.
Have you ever visited a website with a lot of graphics? Then you have likely used Shockwave on that device.
Have you ever looked at a .pdf file on one of your devices? Then you must have used a product like Adobe Reader or Adobe X.
Have you browsed the web? Then you have visited a site that uses an Apache Server.
Does your workplace or school use a firewall like Sonicwall from Dell or a similar product from Xyzel, Cisco?
Do you own an iPhone or an Android?
Do you browse the Internet using Internet Explorer or Chrome, Firefox or Safari?
Then you should take a look at this week’s bulletin from our government: https://www.us-cert.gov/ncas/bulletins/SB13-350
Every month, every week, sometimes daily, our government warns of holes in your device. In this week’s bulletin alone:
13 security problems with Firefox, 7 are critical
7 security problems with Chrome 4 are critical
8 security problems with Internet Explorer, 5 are critical
4 critical security problems with Adobe Air and Shockwave
5 security problems with Windows, 3 are critical
Even the Jiffyyum Kiosk (a proprietary payment system) in California Subway stores has been breeched and hackers can get your name, user ID, and password at Subway. Big deal? No.
The hackers can also pull from the kiosk your credit or debit number, expiration date and CVC code and a not too grainy photo of your face as you use the kiosk. Good for Subway security, but not so good for your identity or credit if the data ends up in the wrong place.
If you use Linux or Apple products you are just as much, if not more, at risk. This is because there are many security breeches noted by our government with Apple and Linux, but there is little or no effort put into addressing Apple and Linux security issues.
Apple simply prefers to avoid any bad press and the legal liability if they admitted a problem existed. Linux is Open Source and considered to be just a little too “wild wes”t to get mainstream attention by those who are ignorant to the power Linux holds.
Apple and Linux have dozens of major security problems every single month that no one addresses.
This week’s security bulletin has three kernel level problems with Linux. They only get a low rating because the operating system is used by so few. When kernel level issues are found in Apple or Windows operating systems they get the highest level of warnings.
It is these kernel level problems that are plaguing the Charlottesville area. When your device is hijacked at the kernel level then you cannot see what is really happening to your data and your antivirus will never report a problem because it is running in a different world than the one you are using.
As national news has begun to verify everything I have been saying, I am not going to spend anymore time trying to prove this is happening. Just this week it was reported nationally that your device camera and microphone can be turned on by hackers at will.
Albemarle County Public School students can have their device turned off, have all the lights dark, or the airplane mode can be turned on, and yet nothing is as it seems. Unless you disconnect the power and pull out the battery, it may be powered on despite looking turned off. The microphone may still be transmitting every sound and the camera sending photos every few seconds to a remote location.
And they often are doing just that.
The data is going to one of three places. Some is going to a computer located at Virginia Tech. Some is going to a local computer bearing a UVA IP address. Most is going to NIST, the National Institute for Standards and technology.
Why? I do not know.
How often? 24/7/365
How much data is being sent? Terabytes every day.
For the techies:
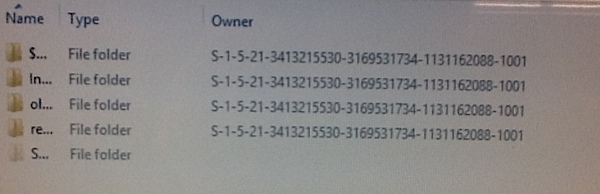
Photo one is an Albemarle County public school student’s computer that has multiple desktop.ini files.
The owner of the files should be the school system, the student, or the computer itself. When Microsoft finds an unknown intruder owning a folder or file it assigns a long number, which is what you see in this photo.
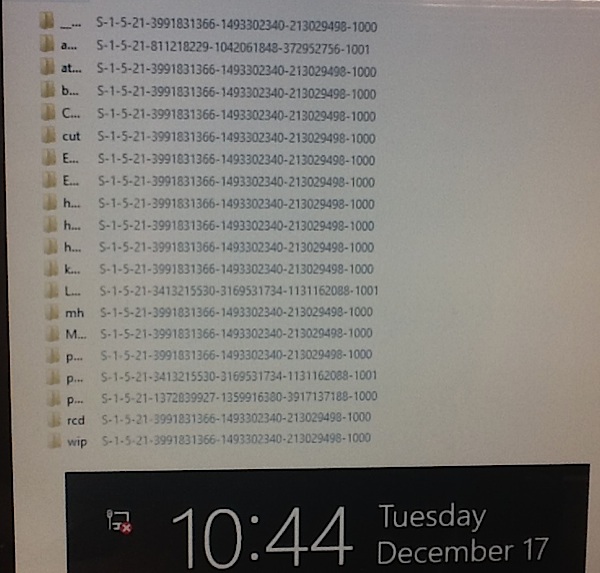
Photo Two, which shows the Windows Eight timestamp, is from a UVA employee’s home computer. When the alternate kernel shell is exposed, voila, also hacked.
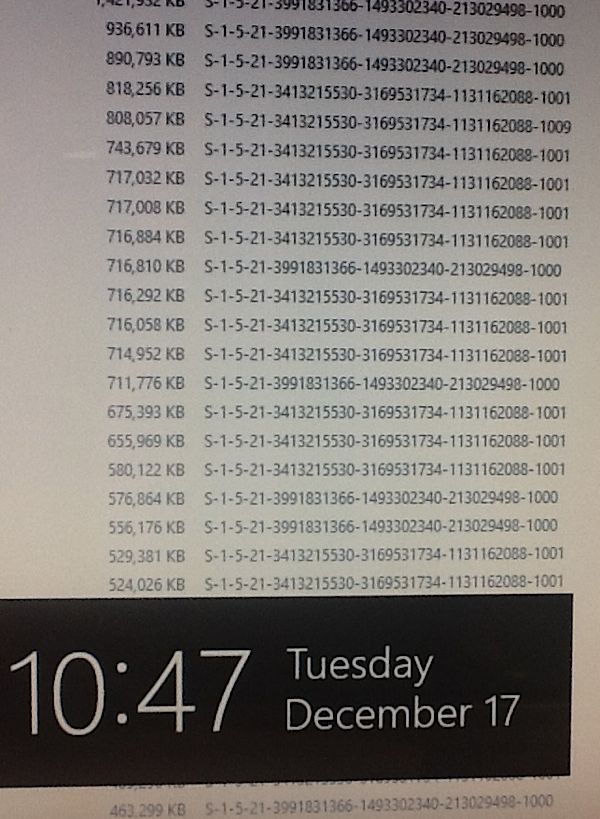
The third photo is from a different UVA employee’s laptop, which the employee is allowed to bring home. Trapping the data being transmitted shows the massive data files, video, and audio that are being sent by this device back to UVA, Virginia Tech and NIST when the device is not on the school network.
Whoever is spying on Albemarle County school children is also spying on UVA employees. I personally was told in the last 24 hours by a local senior computer security expert and a colleague was just told by a former senior federal government technology official, “there is nothing a layman can do about this and even most computer experts can’t stop this from happening.”
It certainly appears it is our own government infecting our devices so it can have audio and video of what we are doing in proximity of our devices. If they can do it, so can the Bulgarians, the Chinese or even our neighbors.
If it is our government, do they think our Albemarle County middle schoolers are terrorists? Unless they can make that argument, is it right that anyone, anyone at all, has the ability to surveil our children?
Don’t accept my word. The media has begun to expose this. While the government may deny these intrusions verbally, by their written words they admit having these capabilities.
FACT: If you live within the reach of Charlottesville area Internet networks then every Internet-connected device in your home is hacked. And the hacking is being done by someone very close to our homes.
Read the security bulletins from our government; Research Stuxnet, IXESHE, Red October, kernel hijacks, java exploits and zero day viruses.
Don’t look over your shoulder. Look straight ahead and smile.







Yikes!
Now in Pt.2, I am now highly suspecting a FRAUD claim by Jim Stern… Why are the folder names truncated by narrowing the column so narrow that the names do not show up? Very suspicious since he is claiming that they are owned by unknown users, which could be the case with the user ID assigned. But why HIDE the folder names in the graphic?
And how does those user ID’s prove that data is being transmitted and to where? I see no proof of anything except some folders with non-assigned user ID’s…
Mr Rumplestiltskin, It seems odd that you use a pseudonym but I use my real name and you throw stones at me. You personally seek for anonymity, (which is what this is all about) but don’t tolerate others right to the same thing.
And, we are protected by the first amendment when they could be cause a security breech by exposing the folder names of their departments file structure.
Try reading up a little bit.
Start at http://support.microsoft.com/kb/243330 to see that these hidden super administrators have the power to do anything they want to do on your computer.
And http://web.nvd.nist.gov/view/vuln/statistics-results?cves=on&query=Microsoft+&cwe_id=CWE-94&pub_date_start_month=-1&pub_date_start_year=-1&pub_date_end_month=-1&pub_date_end_year=-1&mod_date_start_month=-1&mod_date_start_year=-1&mod_date_end_month=-1&mod_date_end_year=-1&cvss_sev_base=&cvss_av=&cvss_ac=&cvss_au=&cvss_c=&cvss_i=&cvss_a=
To see a chart of code injection trends and then you should look at as much on the us cert site as you can. You are smarter than the average American citizen but you need to learn just a little bit about how this is technically possible and in fact exposed by the government in their reports to the world.
But after you learn come back here and post a response. But please don’t just rant, tell us what you find and cite your sources and who you are for all to see. Your writing anonymously and I out in the full view doesn’t work for me, so tell us all who you are and then we can talk some more
anyone by now should know that when use log onto anyone site, data is being exchanged. when you use a computer at work, data is being exchanged. In some cases the business, can sit down and show you how much time is not work related. When by a new program, doesn’t you computer has for permission to run it. ETC. There is nothing new here, the issue is human being become too comfortable using computer, web surfing etc and when they get hit, than they speak out. Do what what some of us do, before log off, delete cookie, clean up your internet file. Don’t go to web site that if got a good viral protection program tell not good idea. If you use view internet as everyone and anyone has access to you business, than you become allot more careful.
“The owner of the files should be the school system, the student, or the computer itself. When Microsoft finds an unknown intruder owning a folder or file it assigns a long number, which is what you see in this photo.”
Actually NO. the s-1-5-21 means that users is an Administrator and the long mysterious part is that users SID. It is pretty easy to trace that SID to a known user that is an Administrator of the system.
You have provided absolutely no evidence of a hack.
Can we see a packet capture?
correction
Actually NO. the s-1-5-21 with and ending value of above 1000means that users were created by and administrator. One that ends in 500 is an Administrator and the long mysterious part is that domain/user SID. It is pretty easy to trace that SID to a known user that is an Administrator of the system.