 I cannot tell you who has gotten in to the ACPS student computers, but I can tell you without a doubt they are infected.
I cannot tell you who has gotten in to the ACPS student computers, but I can tell you without a doubt they are infected.
I can also tell you without a doubt that the staff of ACPS will deny this, the Information Technology Department of ACPS will deny this vehemently, and the Superintendent and the School Board will blindly believe them. Not because they believe the denials, but because they don’t want yet another scandal to rock our schools.
But this is an avalanche that cannot be stopped. The Information Technology Department is not completely incompetent but they are completely in denial and soon the entire school administration will follow suit.
The problems in student computers are extremely hard to understand, even for seasoned professionals, because they are extremely cutting edge encroachments into the operating systems of these ACPS computers and netbooks.
Due to the technical nature of the issue, and the abundance of photographic evidence, this will be a multi-part series. But let’s start here with a few basics:
All but a few of the ACPS student computers and netbooks I have reviewed have an alternate shell installed. This means an infection cannot be detected by ANY current antivirus software, and that all scans, even if done in Safe Mode, will come up clean. It also means that some unknown person or entity could have unfettered access to everything on that computer whenever the computer is connected to the Internet.
It also means that any computer that has shared a network with an ACPS student computer—or has had a USB drive connected to it with data from an ACPS student on it—is potentially infected. So if you have a student who has connected to your home wireless network or has brought homework home on a flash drive, then you are at high risk of this super-infection.
So if I can’t detect it with antivirus software how do I know it is there? And why would ACPS be expected to know it was there, or even believe it was there?
My response is that multiple technology experts have reviewed my conclusions. Some have offered to share their findings with ACPS, only to have the door shut in their faces.
Almost a year and a half ago I brought an infected netbook and laptop computer to the McIntire Office building where the ACPS Information Technology Department is located. Not only did I give them an opportunity to look at the devices, I provided them written information about the compromise. I also I gave ACPS IT the phone number of a Department of Homeland Security contact in Washington DC who had reviewed and validated that there was a serious problem.
They did nothing.
A few weeks later I went back to Central Office to give ACPS IT my child’s devices and the photographic proof that were both infected. But this time I brought with me a member of the Harrisonburg Department of Homeland Security who was willing to meet with the school technology department. The staff member refused to speak with him. A follow up call to the ACPS IT department head trying to set up a meeting with Homeland Security was rebutted with “we will look into it and get back to you but do not want to speak with Homeland Security unless we deem it necessary.”
ACPS never contacted me or the agent in Harrisonburg or the agent in Washington DC. But they did “reimage” the devices. Essentially covering up the problem, at least temporarily.
At this point the expert’s opinion was that the infection was a sophisticated rootkit. But it turns out the experts now say it is likely more sophisticated and more sinister than they thought at that time.
For the technical readers there will be much greater detail in future segments and I will provide more photographic evidence in each of the future segments. For the semi-technical among the readers of the Schilling Show Blog let me give some additional details now.
The most important questions you might be asking are:
How can we see there is a problem?
You have to dig in to the system manually. The way you identify the problem is very different on Apple devices and Windows devices. What you see is also very different from one Operating System to another. For the photos shown below all ACPS netbooks or laptop computers photographed are running Windows 8.
The first clue is the presence of multiple hidden desktop.ini files. In some cases there are as many a four or five, there should either be one or none, never two or more.
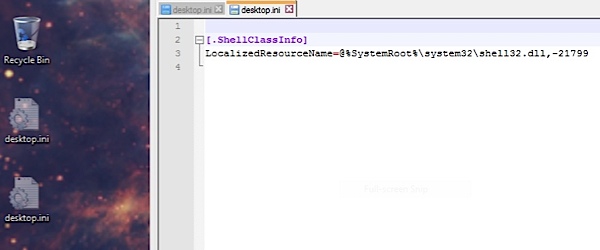
On the right side you can see the instructions in the text of the first file.
The second clue is to look at the actual lines of instructions contained in the desktop initialization files.
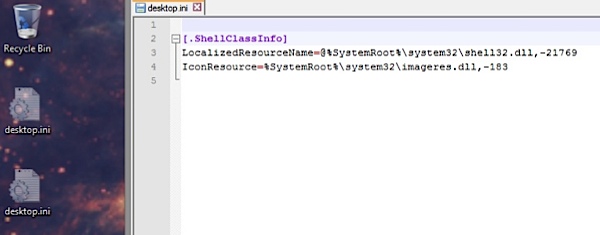
The other desktop.ini files have different commands and the commands change on a completely predictable basis. When you eliminate the compromise in a section of the operating system shell commands it redirects the device to draw its instructions from another place. Where that is will be covered in upcoming segments.
What is happening is these are directing the computers to run and or access different things depending on what the user is doing.
Why don’t automated products don’t find this?
This question is answered partially by those desktop.ini file commands.
When antivirus software is run, the commands don’t show it the places the virus is hidden. Even more sophisticated, if Windows error reporting is initiated, the command does not really report the error to Microsoft and it then reports that no solution is available at this time.
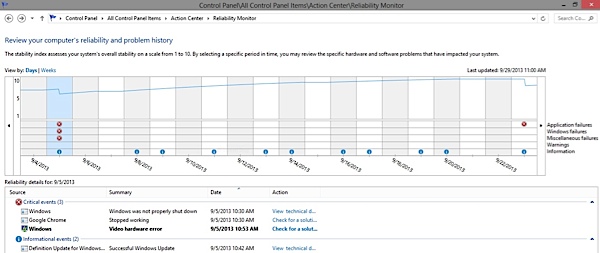
The errors state on the Microsoft Summary that they are the following
1) Windows did not shut down correctly.
2) Google Chrome did not shut down correctly.
3) There was a video hardware error.
In fact when you open the technical details you see something very different.
When you open error one (see below), Windows not shut down correctly, It shows Powerpoint was the problem application. I will go into more details for the technical folks in future segments but note the Locale ID is 1033 and that there is no option to view any faulting file.
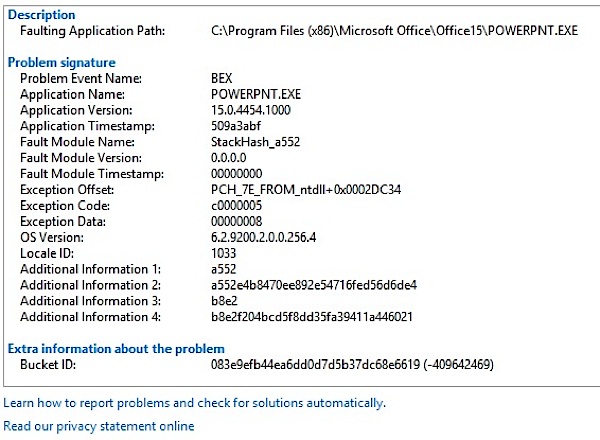
When you open error two (see below), it shows that Chrome did not shut down correctly.
It also shows a that it was a Live Kernel Event (changing the shell commands and making the desktop.ini files change the next time the Internet is accessed). Note this is also in the same exact Locale ID 1033 as referenced above; you can see a copy of the faulting files, but only if you ignore the virus warning and provide the Administrator password.
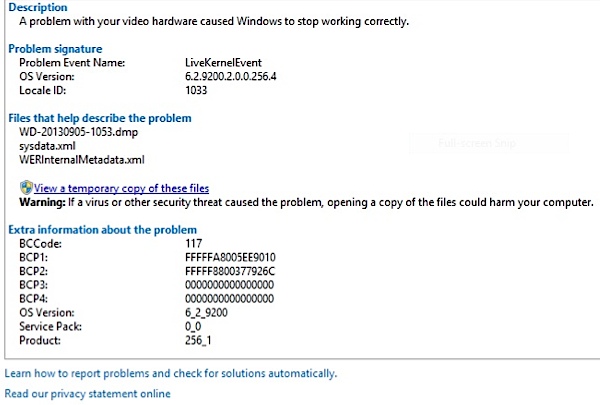
When you open error three, (see below) it shows a video hardware error. But in reality, it wasn’t that at all. It was a Windows Explorer error, and it is still in Locale ID 1033. This time if you want to ignore the security warning and see a copy of the files, you don’t need any special credentials.
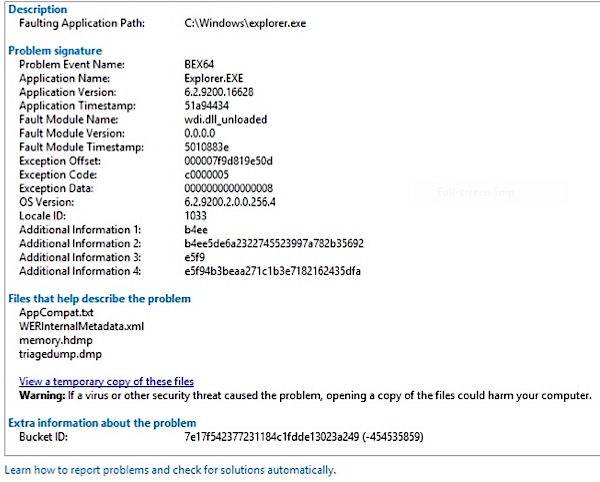
Another key to all of this remaining hidden from users is that if you go back and look a second time the entire record is gone. On second review, the display says that there are no errors that are unresolved, and even scarier, that their have been no errors at all and the system is fine. A screen shot is the only way to document the previously shown errors.
There is more to come. In the upcoming segments I will show:
- Evidence of things hidden on the ACPS netbooks and computers.
- Evidence of Windows Update security downloads falsely reporting they are installed, when they are not.
- Evidence of many other current and potential problems caused by these alternate shell commands.
- More details as to where this compromise hides in these devices, how it is spread and other infections not believed to be related to this being spread by these ACPS devices.
What I can’t tell you now is: who did this, what data is being accessed and where it is going to when the computer connects over the Internet.
Although all data on these ACPS devices CAN be accessed by an outside party, that does not mean it IS being accessed. It does not necessarily mean that that it has spread beyond the nearly 100 devices I have looked at personally—but in fact it has.
An expert computer security firm reviewed this problem and says it can only be stopped through education and with concerted effort. These security experts have all said the solution begins by throwing away the pre-conceived notions that ACPS installed security systems, cloud based security systems and other software are reporting truth to users or even to the ACPS administration.
So, parents, family and friends of ACPS students, and for anyone who has come in contact with ACPS devices: Please be careful with your personal electronic devices and make sure you read all of the follow-up segments.
And, Administration of Albemarle County Public Schools: Let the denials begin.
Who is watching your child in Albemarle County Public Schools? Only the hackers know.







Who is watching your child THROUGH a government issued Albemarle County School computer? Read Jim Stern's frightening investigation…
How do you guys keep the tin foil hats from blowing off of your heads when you guy outside?
How do you guys keep the tin foil hats from blowing off of your heads when you guy outside?
The intellectual level of the Schilling Show is quite low. We hear lots of conspiracy theorists with books to sell, but few thinkers smart enough to merit notice even in the scholarly conservative press, much less to make the liberal media feel threatened and respond. Rob reads my emails on the air when he thinks they can be refuted with a soundbite. He doesn’t read or respond to my detailed follow-up emails, which strongly suggests that he knows he can’t rebut them.
But Rob does do the community a service by giving people like Jim Stern a forum. Prove him wrong if you can. But he’s presented information that the community deserves to see, and for that he deserves our gratitude.
I find Jim Stern’s claims interesting, but not enough details so far and the proof in Pt.1 is not really showing us anything except potential desktop services concerns. No proof of kernel or root kit infection. I hope to see more detail…
But with today’s revelation that the NSA had a backdoor in some RSA number generations, which is HUGE news for those who know, and it proves the “tin foil hat” crowd was RIGHT after all, they DO have access to almost EVERYTHING…